- Joined
- Sep 26, 2021
- Posts
- 7,256
- Main Camera
- Sony

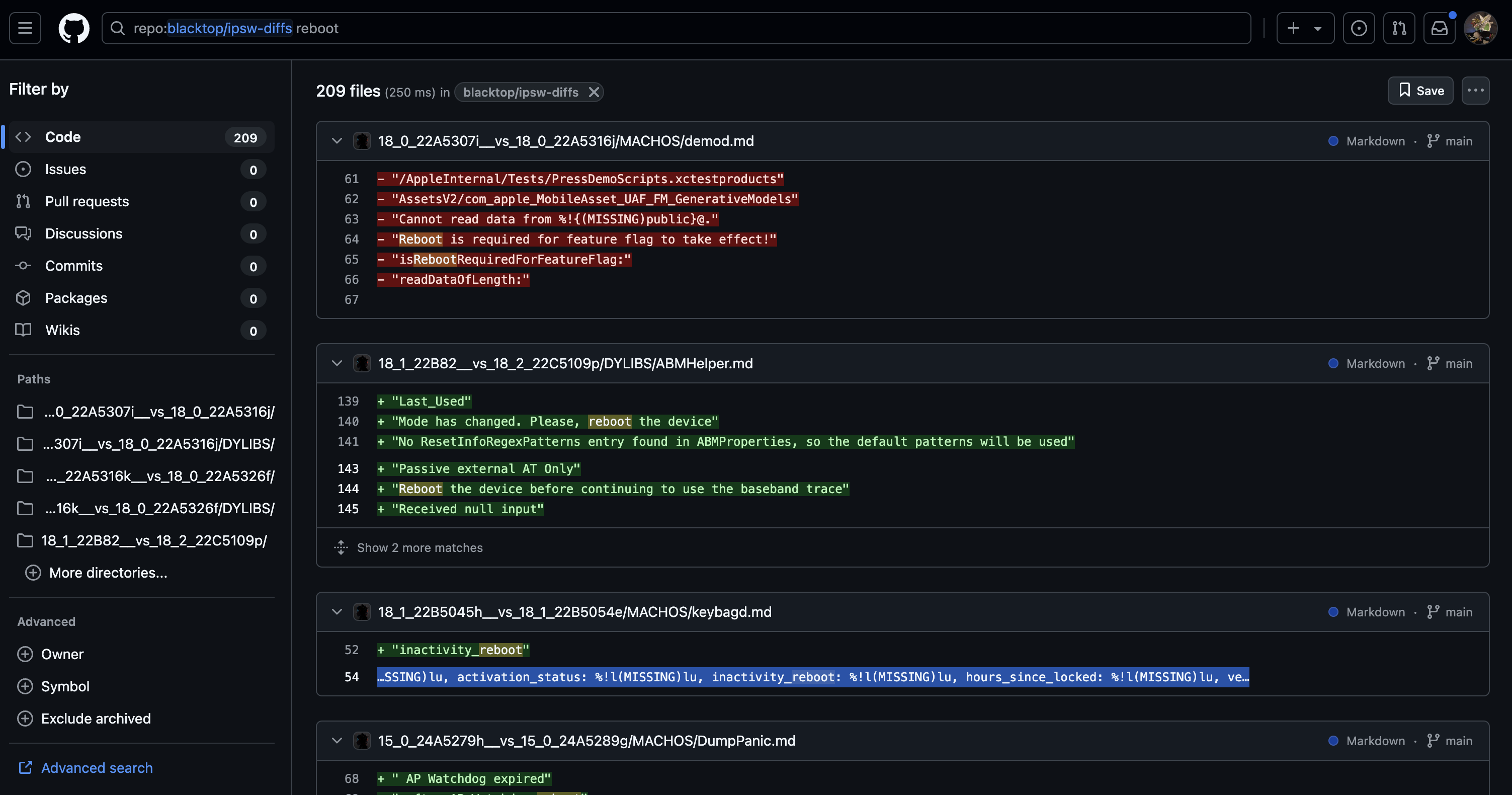
Cops think iPhones are secretly communicating with each other to reboot [U] - 9to5Mac
Update: A security researcher on Mastodon has cracked the case on this, proving that it has nothing to do with...
 9to5mac.com
9to5mac.com
This is a weird story. Cops locking phones in Faraday boxes, etc., claiming that the phones reboot themselves. Then they say that the rebooting may be caused by some magical communication with the cops’ own phones, which somehow tell the locked-up phones to reboot.
Once they reboot, cops can’t easily extract data from the phone.
Assuming it’s true that they are rebooting, and further assuming it isn’t some sort of bug, seems much more likely that Apple instituted some sort of network watchdog timer - after 24 hours of zero network connectivity, they reboot. That would be cool. I don’t believe one iPhone can communicate with another through a Faraday cage.