Jimmyjames
Elite Member
- Joined
- Jul 13, 2022
- Posts
- 1,434
Continuing my series of very niche interests, I was recently considering if anything significant has changed with regard to XNU.
For anyone who doesn’t know, XNU is the name of the kernel in pretty much all of Apple’s products. It’s comprised of the Mach microkernel and quite a bit of FreeBSD’s code. Unlike Mach, XNU isn’t run as a microkernel, but as a more traditional monolithic kernel with loadable kernel modules. Pretty much the standard for mainstream os’s these days. That has its good points and bad points. They are too numerous to go into here, and indeed, my neophyte understanding may be unaware of them, but essentially I would say the current situation gives pretty good performance, all essential low level services are within the kernel, bypassing the need for slower message passing that early iterations of Mach incurred. The main downsides are complexity: the kernel is a very thorny place to venture into, and any small error can wreak havoc. Secondly there is the issue of security. That is, once you are in the kernel, you can pretty much do anything. This can lead to big security and stability problems.
Over time, Apple has locked down kernel access even on macOS to developers. Kexts are increasing difficult or impossible to use. Drivers must be developed in userland using various frameworks Apple has developed. Even useful utilities like Dtrace (an instrumentation and debugging tool) have been restricted. I began to wonder if this restriction was in service of something more ambitious. Not just control, but the ability to slowly migrate from XNU to something more secure, efficient and stable.
There were rumours about an academic project called L4, a very efficient and small microkernel. Indeed, the Secure Enclave uses L4 at its heart. Nothing seemed to happen for while though.
As luck would have it, I also recently saw an article https://www.df-f.com/blog/ios17 which goes into some new features of iOS 17. These are low level features for Apple themself, rather than devs. They are designed primarily to increase security. One thing stood out in the article however:
Very interesting! Could this be a new direction? These “exclave domains” which allow partial compromise of a kernel without all parts being effected. It’s an intriguing and exciting idea to me. Could they spread to other kernel areas?
I’d be interested in any thoughts anyone might have on this, even though I do realise this is not a mainstream area of interest.
For anyone who doesn’t know, XNU is the name of the kernel in pretty much all of Apple’s products. It’s comprised of the Mach microkernel and quite a bit of FreeBSD’s code. Unlike Mach, XNU isn’t run as a microkernel, but as a more traditional monolithic kernel with loadable kernel modules. Pretty much the standard for mainstream os’s these days. That has its good points and bad points. They are too numerous to go into here, and indeed, my neophyte understanding may be unaware of them, but essentially I would say the current situation gives pretty good performance, all essential low level services are within the kernel, bypassing the need for slower message passing that early iterations of Mach incurred. The main downsides are complexity: the kernel is a very thorny place to venture into, and any small error can wreak havoc. Secondly there is the issue of security. That is, once you are in the kernel, you can pretty much do anything. This can lead to big security and stability problems.
Over time, Apple has locked down kernel access even on macOS to developers. Kexts are increasing difficult or impossible to use. Drivers must be developed in userland using various frameworks Apple has developed. Even useful utilities like Dtrace (an instrumentation and debugging tool) have been restricted. I began to wonder if this restriction was in service of something more ambitious. Not just control, but the ability to slowly migrate from XNU to something more secure, efficient and stable.
There were rumours about an academic project called L4, a very efficient and small microkernel. Indeed, the Secure Enclave uses L4 at its heart. Nothing seemed to happen for while though.
As luck would have it, I also recently saw an article https://www.df-f.com/blog/ios17 which goes into some new features of iOS 17. These are low level features for Apple themself, rather than devs. They are designed primarily to increase security. One thing stood out in the article however:
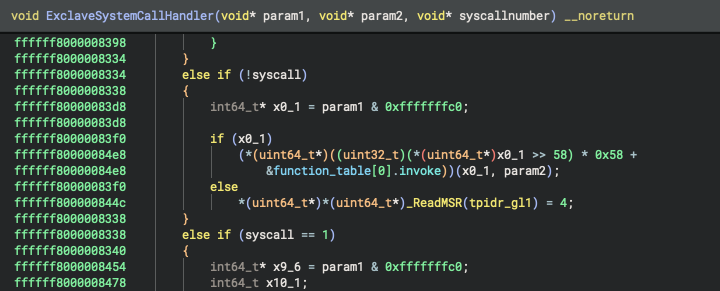
This is in line with the few mentions of "exclaves" spotted elsewhere in strings. It seems Apple's new design is to transition away from the PPL to this new, micro-kernel like architecture, in which XNU's security functionality is refactored and isolated into exclave domains. Those are kept physically separate from XNU proper, so that even a hypothetical kernel compromise would be unable to further jeopardize the integrity of the other exclave components.
Very interesting! Could this be a new direction? These “exclave domains” which allow partial compromise of a kernel without all parts being effected. It’s an intriguing and exciting idea to me. Could they spread to other kernel areas?
I’d be interested in any thoughts anyone might have on this, even though I do realise this is not a mainstream area of interest.