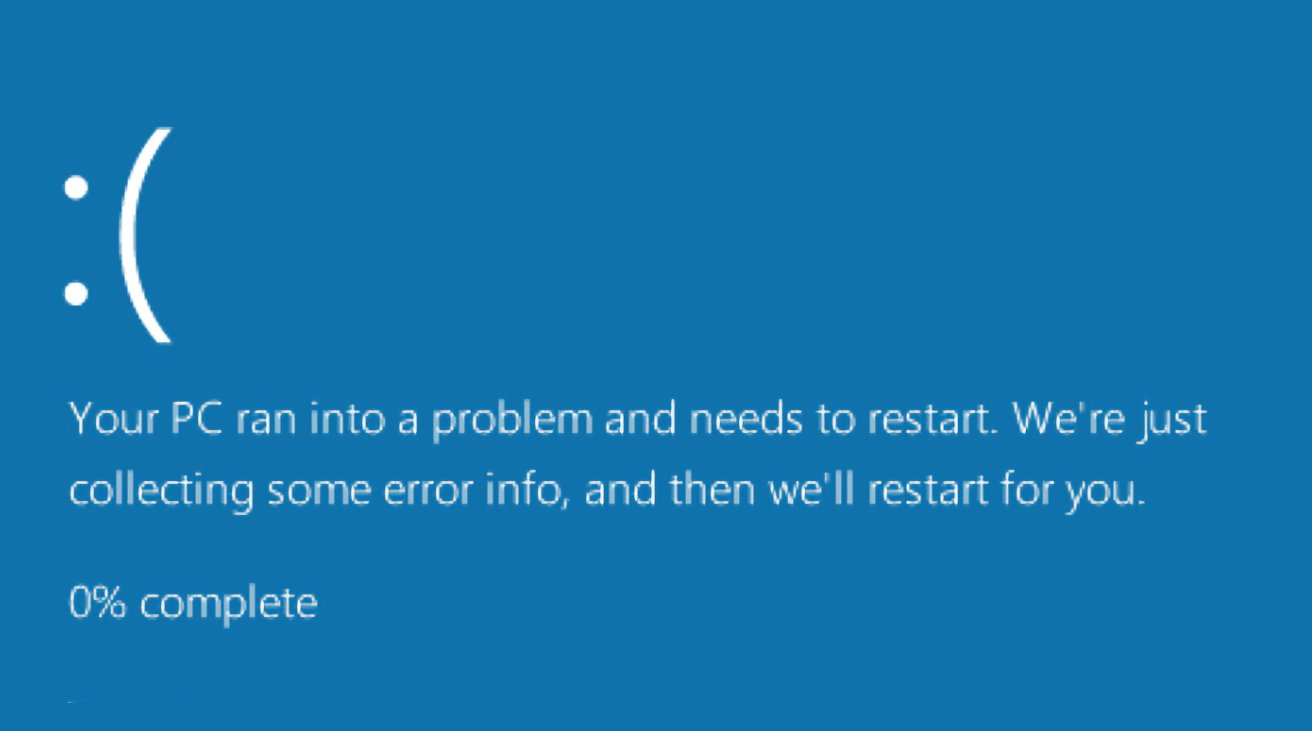
The worldwide outage of Windows PCs was because of European Commission demands, says Microsoft, and we should get used to it.

appleinsider.com
Microsoft seems to blame the EU for the outage. Their argument is they can’t do what Apple did and push this junk out of kernel-space, because the EU requires that third parties have the same access to the kernel that Microsoft does (for Defender).
Of course, they don’t explain why they can’t spin out their own security software into a separate company, or why they can’t build in SDKs that everyone, including Defender, can use.
But, in any case, I always like blaming the EU.

www.tomshardware.com